How Spyware Works
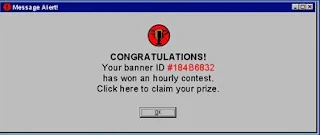
Spyware is malicious software that can hijack and cripple your computer. It has been known to masquerade as a prize-notification pop-up window, like the example above and is one method of online identity theft and virus spreading.They're designed to track your Internet habits, nag you with unwanted sales offers or generate traffic for their host Web site. According to some estimates, more than 80 percent of all personal computers are infected with some kind of spyware.
Generally isn't designed to damage your computer. Spyware is defined broadly as any program that gets into your computer without your permission and hides in the background while it makes unwanted changes to your user experience. The damage it does is more a by-product of its main mission, which is to serve you targeted advertisements or make your browser display certain sites or search results.
At present, most spyware targets only the Windows operating system. Some of the more notorious spyware threats include Trymedia, Nuvens, Estalive, Hotbar and New.Net.Domain plugin.
The most common way to infect a computer with spyware is to trick the user into installing it themselves. A user goes to a website and there’s a button that says “Hey, install our fun new game!” And you click on it thinking it’s just a fun new game, but by clicking on it you effectively give that software permission to modify your system. That permission could be totally innocent, but it could also do other things, and you don’t know what those things are.
People should be very wary of anything that’s asking you to install something on your computer, or have access to files on your computer. Your answer should almost always be no, unless you know exactly what you’re getting.
Several free anti-spyware tools that can scan your hard drive, flash drive, external hard drive, etc. to remove spyware. Some of them only work when you manually start the scan but others will monitor your computer all the time to make sure spyware can't modify your computer or monitor your information.
Below are several free anti-spyware tools that can scan your hard drive, flash drive, external hard drive, etc. to remove spyware. Some of them only work when you manually start the scan but others will monitor your computer all the time to make sure spyware can't modify your computer or monitor your information.
Note: All the programs mentioned below are known to scan for spyware but they might not scan for other things like viruses. Other scanners remove some kinds of malware but not spyware, so we've omitted those from this list.
Malwarebytes
Malwarebytes is another big-hitter when it comes to cleaning up spyware. It's easy to use and tends to find a lot more malicious items than similar programs.
Malwarebytes is an anti-malware software for Microsoft Windows, MacOS and Android that finds and removes malware made by Malwarebytes Corporation. It is available in a free version, which scans for and removes malware when started manually and a paid version, which additionally provides scheduled scans, real-time protection and a flash-memory scanner.
It scans through registry values and keys, files, and running processes, plus includes a heuristics analyzer to find potentially unwanted programs.
When the scan is complete, it's really easy to tell where the spyware was found and selecting the ones to quarantine is just a click or two away.Malwarebytes can also scan individual files and folders as well as whole hard drives, with the right-click context menu in Windows Explorer. There's an option to scan within archives, ignore certain files/folders, and to scan for rootkits too.
SpywareBlaster
SpywareBlaster is different from the rest of these programs since it doesn't scan for existing spyware, though true to its name, it does "blast" new threats before they can reach your system.
SpywareBlaster prevents the download, installation and execution of most spyware, adware, browser hijackers, dialers and other malicious programs based on ActiveX. SpywareBlaster works on the basis of "blacklists" (Activating the "Killbit") Clsid of known malware programs, effectively preventing them from infecting the protected computer. This approach differs from many other anti-spyware programs, which typically offer the user a chance to scan the hard drive and computer memory to remove unwanted software after it has been installed.
The way it works is that you can enable protection for your web browsers to protect against malicious scripts, exploits, and cookies that track your web behavior. It does this by enabling a pre-made list of blockades (which you can update manually at any time) against certain websites, cookies, and scripts.
SpywareBlaster also allows the user to prevent privacy risks such as tracking cookies. Another feature is the ability to restrict the actions of websites known as distributors of adware and spyware. SpywareBlaster supports several web browsers, including Internet Explorer, Mozilla Firefox and Google Chrome.
SpywareBlaster is currently distributed as freeware, for non-commercial users.
Avast Antivirus is a computer security application, which provides protection against a range of potential threats, including viruses, spyware, malware and ransomware. It is currently recognized as the most popular antivirus program on the market and the free version of the software is suitable for personal and home use.
Avast Free Antivirus is an efficient and comprehensive antivirus program. It is one of the most popular antivirus programs available, thanks to the reliable and trustworthy brand that Avast have created. The key features that continue to make Avast Free Antivirus so popular are the easy UI, optimized scanning options and continuously updated database of virus definitions.
Avast can detect and remove spyware before you even know it's on your computer. What makes it different than the two from above is that it's always on and always watching for new threats.
There are lots of settings you can adjust in Avast, like to enable CyberCapture to block unrecognized files, use Hardened Mode to really lock down on security, scan for potentially unwanted programs, scan from Windows Explorer, exclude files/folders/URLs from scans, and lots more.
The software is completely free and, in terms of virus protection, is sufficient for most users. The free version is designed for personal use and offers the same level of protection as the paid 'Pro' version of the software. However the 'Pro' version adds a number of peripheral features and can be used for commercial purposes.
AVG AntiVirus Free
AVG Antivirus Free is an antimalware security suite that includes an active file and email scanner, plus Web browsing protection.
It's a another popular antivirus program that serves as a full malware scanner, checking for and removing not only spyware but also ransomware, viruses, and more. all automatically and for free.
It now includes real-time security updates, scans for both malware and performance issues, and even catches malicious downloads before they reach your PC. It’s also got an all-new, refreshingly simple design that shows you exactly how you’re protected. All of this, and it still won’t slow you down!
AVG provides not only protection for your computer but also for your web activity and email. You can perform a full system scan, a boot-time scan, or a custom scan, but there's also a dedicated button that instantly starts a check for spyware on all your removable devices.
Another unique feature in AVG is its Deep Scan option that runs a much slower but also more thorough scan, a good option if nothing else seems to get rid of the spyware. You can configure it to recognize files by their cntent and not their extension, which is ideal if the spyware is using a hidden/false file extension.
The Deep Scan option can also open and scan through over 20 archive file types, much more than most other spyware scanners that usually just support the popular ones (ZIP and RAR).
Although AVG AntiVirus Free provides the same core virus protection as the 'Pro' edition, some peripheral services are missing, when compared to the 'Pro' version. These include Online Shield, which is a feature used to offer extra protection against harmful downloads, and Data Safe, which is an encryption tool for personal files.
Download AVG AntiVirus Free
Trend Micro HouseCall
Trend Micro HouseCall is a powerful, free software only available for Windows, that belongs to the category Security software with subcategory Anti-virus (more specifically Generic) and has been created by Trend Micro.
HouseCall is a software that requires less storage than most software in the section Security software. It's a very popular software in United States, Canada, and Australia.
HouseCall is our highly popular scanner for identifying and removing viruses, Trojans, worms, unwanted browser plugins, and other malware. It’s quick and easy to use and will work regardless of your existing security solution. What’s more, HouseCall is powered by Trend Micro’s leading cloud-based threat prevention service the Smart Protection Network, enabling it to spot and block all the latest malware.
Users whose machines may have been infected will be notified by Facebook with the option to download the free version of HouseCall to scan and remove the offending malware. They can continue to use Facebook while the scan is taking place and, once complete, a message will pop-up to notify them if the clean-up was successful.
Download Trend Micro HouseCall















